To obtain the API token in the SentinelOne console, click the Settings tab, and then click Users. If this information is lost before it is submitted to Arctic Wolf on the Distributed by an MIT license. This API key expires and will need to be regenerated every six months. 99 - Admin in Site CORP-servers-windows of Account CORP", "Global / CORP / CORP-servers-windows / Env. The third categorization field in the hierarchy. Detects actions caused by the RedMimicry Winnti playbook. To review, open the file in an editor that reveals hidden Unicode characters. To install it: moduleInstall-Module -Name PSFalcon Update-Module -Name PSFalcon Script - CS.ps1 param ( Detects persitence via netsh helper. Package manager (eg: apt, yum) can be altered to install malicious software. Detects suspicious PowerShell invocation command parameters, Detects new commands that add new printer port which point to suspicious file. WebMimecast API Build Powerful Applications and Integrations Plug into the world's largest cyber resilience ecosystem. Many Git commands accept both tag and branch names, so creating this branch may cause unexpected behavior. ), Detects download of certain file types from hosts in suspicious TLDs. WebSentinelOne currently offers the following integrations: SentinelOne kann durch Syslog-Feeds oder ber unsere API problemlos mit Datenanalyse-Tools wie SIEM integriert Odbierz DARMOWE przedmioty w ulubionej grze!  This rule is here for quickwins as it obviously has many blind spots. Detects netsh commands that enable a port forwarding between to hosts. 01 - Prod in Site corp-servers-windows of Account corp\", \"fullScopeDetailsPath\": \"Global / corp / corp-servers-windows / Env. Detection of accesses to Microsoft Outlook registry hive, which might contain sensitive information. LD_PRELOAD and LD_LIBRARY_PATH are environment variables used by the Operating System at the runtime to load shared objects (library.ies) when executing a new process, attacker can overwrite this variable to attempts a privileges escalation. ", "84580370c58b1b0c9e4138257018fd98efdf28ba", "\"C:\\Users\\user\\AppData\\Local\\WebEx\\WebexHost.exe\" /daemon /runFrom=autorun", "C:\\Users\\user\\AppData\\Local\\WebEx\\WebexHost_old.exe", "d8efbbfab923ad72057d165dc30f2c0d39a4f4d2dcb7d6fa8a8c9c5b406fcb23", "\"C:\\Users\\user\\AppData\\Local\\WebEx\\WebexHost.exe\" /job=upgradeClient /channel=2af416334939280c", "5b1bbda6c8d9bb6e49e5e7c49909d48d5d35658a", "e89dd9db7c5f93ab2fd216d36e7432ea3b418b5df0191d4849fdb1967b2f6e2e", "C:\\Users\\user\\AppData\\Local\\WebEx\\WebEx64\\Meetings\\atucfobj.dll", "Ecriture d'une dll webex \"atucfobj.dll\" inconnu du syst\u00e8me sur le parc. Microsoft Sentinel delivers intelligent security analytics and threat intelligence across the enterprise, providing a single solution for alert detection, threat visibility, Powershell's uploadXXX functions are a category of methods which can be used to exfiltrate data through native means on a Windows host. Detects PowerShell commands aiming to exclude path, process, IP address, or extension from scheduled and real-time scanning. By using the standard SentinelOne EDR logs collection by API, you will be provided with high level information on detection and investigation of your EDR. 99 - Admin\", \"osFamily\": \"Windows\", \"scopeLevel\": \"Group\", \"scopeName\": \"Env. Show me the third-party integrations you've already built yourself and tell me where to get them. Event type.
This rule is here for quickwins as it obviously has many blind spots. Detects netsh commands that enable a port forwarding between to hosts. 01 - Prod in Site corp-servers-windows of Account corp\", \"fullScopeDetailsPath\": \"Global / corp / corp-servers-windows / Env. Detection of accesses to Microsoft Outlook registry hive, which might contain sensitive information. LD_PRELOAD and LD_LIBRARY_PATH are environment variables used by the Operating System at the runtime to load shared objects (library.ies) when executing a new process, attacker can overwrite this variable to attempts a privileges escalation. ", "84580370c58b1b0c9e4138257018fd98efdf28ba", "\"C:\\Users\\user\\AppData\\Local\\WebEx\\WebexHost.exe\" /daemon /runFrom=autorun", "C:\\Users\\user\\AppData\\Local\\WebEx\\WebexHost_old.exe", "d8efbbfab923ad72057d165dc30f2c0d39a4f4d2dcb7d6fa8a8c9c5b406fcb23", "\"C:\\Users\\user\\AppData\\Local\\WebEx\\WebexHost.exe\" /job=upgradeClient /channel=2af416334939280c", "5b1bbda6c8d9bb6e49e5e7c49909d48d5d35658a", "e89dd9db7c5f93ab2fd216d36e7432ea3b418b5df0191d4849fdb1967b2f6e2e", "C:\\Users\\user\\AppData\\Local\\WebEx\\WebEx64\\Meetings\\atucfobj.dll", "Ecriture d'une dll webex \"atucfobj.dll\" inconnu du syst\u00e8me sur le parc. Microsoft Sentinel delivers intelligent security analytics and threat intelligence across the enterprise, providing a single solution for alert detection, threat visibility, Powershell's uploadXXX functions are a category of methods which can be used to exfiltrate data through native means on a Windows host. Detects PowerShell commands aiming to exclude path, process, IP address, or extension from scheduled and real-time scanning. By using the standard SentinelOne EDR logs collection by API, you will be provided with high level information on detection and investigation of your EDR. 99 - Admin\", \"osFamily\": \"Windows\", \"scopeLevel\": \"Group\", \"scopeName\": \"Env. Show me the third-party integrations you've already built yourself and tell me where to get them. Event type.  ", "{\"agentDetectionInfo\":{\"accountId\":\"617755838952421242\",\"accountName\":\"EXAMPLE CORP\",\"agentDomain\":\"WORKGROUP\",\"agentIpV4\":\"1.1.1.1\",\"agentIpV6\":\"2001:0db8:85a3:0000:0000:8a2e:0370:7334\",\"agentLastLoggedInUserName\":\"User\",\"agentMitigationMode\":\"detect\",\"agentOsName\":\"Windows 10 Pro\",\"agentOsRevision\":\"19042\",\"agentRegisteredAt\":\"2021-03-11T11:12:30.665887Z\",\"agentUuid\":\"e50b53c856f041bab326d621d61db4f8\",\"agentVersion\":\"4.6.12.241\",\"externalIp\":\"2.2.2.2\",\"groupId\":\"1107851598374945694\",\"groupName\":\"Default Group\",\"siteId\":\"1107851598358168475\",\"siteName\":\"Sekoia.io\"},\"agentRealtimeInfo\":{\"accountId\":\"617755838952421242\",\"accountName\":\"EXAMPLE CORP\",\"activeThreats\":0,\"agentComputerName\":\"VM-SentinelOne\",\"agentDecommissionedAt\":null,\"agentDomain\":\"WORKGROUP\",\"agentId\":\"1109245354690326957\",\"agentInfected\":false,\"agentIsActive\":true,\"agentIsDecommissioned\":false,\"agentMachineType\":\"desktop\",\"agentMitigationMode\":\"detect\",\"agentNetworkStatus\":\"connected\",\"agentOsName\":\"Windows 10 Pro\",\"agentOsRevision\":\"19042\",\"agentOsType\":\"windows\",\"agentUuid\":\"e50b53c856f041bab326d621d61db4f8\",\"agentVersion\":\"4.6.12.241\",\"groupId\":\"1107851598374945694\",\"groupName\":\"Default Group\",\"networkInterfaces\":[{\"id\":\"1109245354698715566\",\"inet\":[\"1.1.1.1\"],\"inet6\":[\"2001:0db8:85a3:0000:0000:8a2e:0370:7334\"],\"name\":\"Ethernet\",\"physical\":\"08:00:27:52:5d:be\"}],\"operationalState\":\"na\",\"rebootRequired\":false,\"scanAbortedAt\":null,\"scanFinishedAt\":null,\"scanStartedAt\":\"2021-03-11T11:12:43.266673Z\",\"scanStatus\":\"started\",\"siteId\":\"1107851598358168475\",\"siteName\":\"Sekoia.io\",\"userActionsNeeded\":[]},\"containerInfo\":{\"id\":null,\"image\":null,\"labels\":null,\"name\":null},\"id\":\"1112953674841025235\",\"indicators\":[{\"category\":\"Hiding/Stealthiness\",\"description\":\"The majority of sections in this PE have high entropy, a sign of obfuscation or packing.\",\"ids\":[29],\"tactics\":[]},{\"category\":\"General\",\"description\":\"This binary imports functions used to raise kernel exceptions.\",\"ids\":[24],\"tactics\":[]},{\"category\":\"Hiding/Stealthiness\",\"description\":\"This binary may contain encrypted or compressed data as measured by high entropy of the sections (greater than 6.8).\",\"ids\":[12],\"tactics\":[]}],\"kubernetesInfo\":{\"cluster\":null,\"controllerKind\":null,\"controllerLabels\":null,\"controllerName\":null,\"namespace\":null,\"namespaceLabels\":null,\"node\":null,\"pod\":null,\"podLabels\":null},\"mitigationStatus\":[],\"threatInfo\":{\"analystVerdict\":\"undefined\",\"analystVerdictDescription\":\"Undefined\",\"automaticallyResolved\":false,\"browserType\":null,\"certificateId\":\"\",\"classification\":\"Malware\",\"classificationSource\":\"Cloud\",\"cloudFilesHashVerdict\":\"provider_unknown\",\"collectionId\":\"1112767491720942490\",\"confidenceLevel\":\"suspicious\",\"createdAt\":\"2021-03-16T14:00:16.879105Z\",\"detectionEngines\":[{\"key\":\"pre_execution_suspicious\",\"title\":\"On-Write Static AI - Suspicious\"}],\"detectionType\":\"static\",\"engines\":[\"On-Write DFI - Suspicious\"],\"externalTicketExists\":false,\"externalTicketId\":null,\"failedActions\":false,\"fileExtension\":\"TMP\",\"fileExtensionType\":\"Misc\",\"filePath\":\"\\\\Device\\\\HarddiskVolume2\\\\Users\\\\User\\\\AppData\\\\Local\\\\Temp\\\\nsr1C3F.tmp\\\\nsh29ED.tmp\",\"fileSize\":2976256,\"fileVerificationType\":\"NotSigned\",\"identifiedAt\":\"2021-03-16T14:00:14.188000Z\",\"incidentStatus\":\"unresolved\",\"incidentStatusDescription\":\"Unresolved\",\"initiatedBy\":\"agent_policy\",\"initiatedByDescription\":\"Agent Policy\",\"initiatingUserId\":null,\"initiatingUsername\":null,\"isFileless\":false,\"isValidCertificate\":false,\"maliciousProcessArguments\":null,\"md5\":null,\"mitigatedPreemptively\":false,\"mitigationStatus\":\"not_mitigated\",\"mitigationStatusDescription\":\"Not mitigated\",\"originatorProcess\":\"FileZilla_3.53.0_win64_sponsored-setup.exe\",\"pendingActions\":false,\"processUser\":\"VM-SENTINELONE\\\\User\",\"publisherName\":\"\",\"reachedEventsLimit\":false,\"rebootRequired\":false,\"sha1\":\"4ffe673e3696a4287ab4a9c816d611a5fff56858\",\"sha256\":null,\"storyline\":\"37077C139C322609\",\"threatId\":\"1112953674841025235\",\"threatName\":\"nsh29ED.tmp\",\"updatedAt\":\"2021-03-16T14:00:16.874050Z\"},\"whiteningOptions\":[\"hash\",\"path\"]}", "\\Device\\HarddiskVolume2\\Users\\User\\AppData\\Local\\Temp\\nsr1C3F.tmp\\nsh29ED.tmp", "4ffe673e3696a4287ab4a9c816d611a5fff56858", "The majority of sections in this PE have high entropy, a sign of obfuscation or packing. The SentinelOne App for Sumo Logic provides security professionals with a comprehensive view of their organization's security posture. Detects popular file extensions in commands obfuscated in base64 run through the EncodedCommand option. Today. Detects various Follina vulnerability exploitation techniques. Detects from the command lines or the registry, changes that indicate unwanted modifications to registry keys that disable important Internet Explorer security features. Detects the exploitation of CVE-2020-0688. SEKOIA.IO x SentinelOne on ATT&CK Navigator, ASLR is a security feature used by the Operating System to mitigate memory exploit, attacker might want to disable it. Detects a command-line interaction with the KeePass Config XML file. Please find bellow a limited list of field types that are available with SentinelOne default EDR logs: And depending on the context of the log, additional content could be available, such as: For advanced log collection, we suggest you to use SentinelOne Deep Visibility kafka option, as described offered by the SentinelOne DeepVisibility integration. This module serves to abstract away the details of interacting with SentinelOnes API endpoints in such a way that is consistent with PowerShell nomenclature. Detects Raccoon Stealer 2.0 malware downloading legitimate third-party DLLs from its C2 server. Information about the SentinelOne agent installed, In the SentinelOne management console, go to. ", "Agent Disabled Because of Database Corruption", "Group Env. The name of the scheduled task used by these malware is very specific (Updates/randomstring). SentinelOne.psm1 Detect threats based on indicators of compromise (IOCs) collected by SEKOIA's Threat and Detection Research team. Set Up the Integration in Perch. :warning: **As of 2022-11, This module has only been tested using PowerShell 5.1. Additionally, PowerShells verb-noun nomenclature is respected. Log in to the Management Console as an Admin. **Select folder:** Choose a folder from your workspace or browse to one that contains your function app.\n\n\tb. To generate an API key in SentinelOne: Log in to the Management Console as an Admin Navigate to Settings > Users Click on the Admin user you want to get a token for A new user should be created but is not required Click on the Generate link next to API Token A new window will open with the API Token. Detects interaction with the file NTDS.dit through command line. Keep known and unknown malware and other bad programs out of endpoints.
", "{\"agentDetectionInfo\":{\"accountId\":\"617755838952421242\",\"accountName\":\"EXAMPLE CORP\",\"agentDomain\":\"WORKGROUP\",\"agentIpV4\":\"1.1.1.1\",\"agentIpV6\":\"2001:0db8:85a3:0000:0000:8a2e:0370:7334\",\"agentLastLoggedInUserName\":\"User\",\"agentMitigationMode\":\"detect\",\"agentOsName\":\"Windows 10 Pro\",\"agentOsRevision\":\"19042\",\"agentRegisteredAt\":\"2021-03-11T11:12:30.665887Z\",\"agentUuid\":\"e50b53c856f041bab326d621d61db4f8\",\"agentVersion\":\"4.6.12.241\",\"externalIp\":\"2.2.2.2\",\"groupId\":\"1107851598374945694\",\"groupName\":\"Default Group\",\"siteId\":\"1107851598358168475\",\"siteName\":\"Sekoia.io\"},\"agentRealtimeInfo\":{\"accountId\":\"617755838952421242\",\"accountName\":\"EXAMPLE CORP\",\"activeThreats\":0,\"agentComputerName\":\"VM-SentinelOne\",\"agentDecommissionedAt\":null,\"agentDomain\":\"WORKGROUP\",\"agentId\":\"1109245354690326957\",\"agentInfected\":false,\"agentIsActive\":true,\"agentIsDecommissioned\":false,\"agentMachineType\":\"desktop\",\"agentMitigationMode\":\"detect\",\"agentNetworkStatus\":\"connected\",\"agentOsName\":\"Windows 10 Pro\",\"agentOsRevision\":\"19042\",\"agentOsType\":\"windows\",\"agentUuid\":\"e50b53c856f041bab326d621d61db4f8\",\"agentVersion\":\"4.6.12.241\",\"groupId\":\"1107851598374945694\",\"groupName\":\"Default Group\",\"networkInterfaces\":[{\"id\":\"1109245354698715566\",\"inet\":[\"1.1.1.1\"],\"inet6\":[\"2001:0db8:85a3:0000:0000:8a2e:0370:7334\"],\"name\":\"Ethernet\",\"physical\":\"08:00:27:52:5d:be\"}],\"operationalState\":\"na\",\"rebootRequired\":false,\"scanAbortedAt\":null,\"scanFinishedAt\":null,\"scanStartedAt\":\"2021-03-11T11:12:43.266673Z\",\"scanStatus\":\"started\",\"siteId\":\"1107851598358168475\",\"siteName\":\"Sekoia.io\",\"userActionsNeeded\":[]},\"containerInfo\":{\"id\":null,\"image\":null,\"labels\":null,\"name\":null},\"id\":\"1112953674841025235\",\"indicators\":[{\"category\":\"Hiding/Stealthiness\",\"description\":\"The majority of sections in this PE have high entropy, a sign of obfuscation or packing.\",\"ids\":[29],\"tactics\":[]},{\"category\":\"General\",\"description\":\"This binary imports functions used to raise kernel exceptions.\",\"ids\":[24],\"tactics\":[]},{\"category\":\"Hiding/Stealthiness\",\"description\":\"This binary may contain encrypted or compressed data as measured by high entropy of the sections (greater than 6.8).\",\"ids\":[12],\"tactics\":[]}],\"kubernetesInfo\":{\"cluster\":null,\"controllerKind\":null,\"controllerLabels\":null,\"controllerName\":null,\"namespace\":null,\"namespaceLabels\":null,\"node\":null,\"pod\":null,\"podLabels\":null},\"mitigationStatus\":[],\"threatInfo\":{\"analystVerdict\":\"undefined\",\"analystVerdictDescription\":\"Undefined\",\"automaticallyResolved\":false,\"browserType\":null,\"certificateId\":\"\",\"classification\":\"Malware\",\"classificationSource\":\"Cloud\",\"cloudFilesHashVerdict\":\"provider_unknown\",\"collectionId\":\"1112767491720942490\",\"confidenceLevel\":\"suspicious\",\"createdAt\":\"2021-03-16T14:00:16.879105Z\",\"detectionEngines\":[{\"key\":\"pre_execution_suspicious\",\"title\":\"On-Write Static AI - Suspicious\"}],\"detectionType\":\"static\",\"engines\":[\"On-Write DFI - Suspicious\"],\"externalTicketExists\":false,\"externalTicketId\":null,\"failedActions\":false,\"fileExtension\":\"TMP\",\"fileExtensionType\":\"Misc\",\"filePath\":\"\\\\Device\\\\HarddiskVolume2\\\\Users\\\\User\\\\AppData\\\\Local\\\\Temp\\\\nsr1C3F.tmp\\\\nsh29ED.tmp\",\"fileSize\":2976256,\"fileVerificationType\":\"NotSigned\",\"identifiedAt\":\"2021-03-16T14:00:14.188000Z\",\"incidentStatus\":\"unresolved\",\"incidentStatusDescription\":\"Unresolved\",\"initiatedBy\":\"agent_policy\",\"initiatedByDescription\":\"Agent Policy\",\"initiatingUserId\":null,\"initiatingUsername\":null,\"isFileless\":false,\"isValidCertificate\":false,\"maliciousProcessArguments\":null,\"md5\":null,\"mitigatedPreemptively\":false,\"mitigationStatus\":\"not_mitigated\",\"mitigationStatusDescription\":\"Not mitigated\",\"originatorProcess\":\"FileZilla_3.53.0_win64_sponsored-setup.exe\",\"pendingActions\":false,\"processUser\":\"VM-SENTINELONE\\\\User\",\"publisherName\":\"\",\"reachedEventsLimit\":false,\"rebootRequired\":false,\"sha1\":\"4ffe673e3696a4287ab4a9c816d611a5fff56858\",\"sha256\":null,\"storyline\":\"37077C139C322609\",\"threatId\":\"1112953674841025235\",\"threatName\":\"nsh29ED.tmp\",\"updatedAt\":\"2021-03-16T14:00:16.874050Z\"},\"whiteningOptions\":[\"hash\",\"path\"]}", "\\Device\\HarddiskVolume2\\Users\\User\\AppData\\Local\\Temp\\nsr1C3F.tmp\\nsh29ED.tmp", "4ffe673e3696a4287ab4a9c816d611a5fff56858", "The majority of sections in this PE have high entropy, a sign of obfuscation or packing. The SentinelOne App for Sumo Logic provides security professionals with a comprehensive view of their organization's security posture. Detects popular file extensions in commands obfuscated in base64 run through the EncodedCommand option. Today. Detects various Follina vulnerability exploitation techniques. Detects from the command lines or the registry, changes that indicate unwanted modifications to registry keys that disable important Internet Explorer security features. Detects the exploitation of CVE-2020-0688. SEKOIA.IO x SentinelOne on ATT&CK Navigator, ASLR is a security feature used by the Operating System to mitigate memory exploit, attacker might want to disable it. Detects a command-line interaction with the KeePass Config XML file. Please find bellow a limited list of field types that are available with SentinelOne default EDR logs: And depending on the context of the log, additional content could be available, such as: For advanced log collection, we suggest you to use SentinelOne Deep Visibility kafka option, as described offered by the SentinelOne DeepVisibility integration. This module serves to abstract away the details of interacting with SentinelOnes API endpoints in such a way that is consistent with PowerShell nomenclature. Detects Raccoon Stealer 2.0 malware downloading legitimate third-party DLLs from its C2 server. Information about the SentinelOne agent installed, In the SentinelOne management console, go to. ", "Agent Disabled Because of Database Corruption", "Group Env. The name of the scheduled task used by these malware is very specific (Updates/randomstring). SentinelOne.psm1 Detect threats based on indicators of compromise (IOCs) collected by SEKOIA's Threat and Detection Research team. Set Up the Integration in Perch. :warning: **As of 2022-11, This module has only been tested using PowerShell 5.1. Additionally, PowerShells verb-noun nomenclature is respected. Log in to the Management Console as an Admin. **Select folder:** Choose a folder from your workspace or browse to one that contains your function app.\n\n\tb. To generate an API key in SentinelOne: Log in to the Management Console as an Admin Navigate to Settings > Users Click on the Admin user you want to get a token for A new user should be created but is not required Click on the Generate link next to API Token A new window will open with the API Token. Detects interaction with the file NTDS.dit through command line. Keep known and unknown malware and other bad programs out of endpoints.  Detects changes on Windows Firewall configuration. This technique is used by the Agent Tesla RAT, among others. No signatures mean Windows Defender will be less effective (or completely useless depending on the option used).
Detects changes on Windows Firewall configuration. This technique is used by the Agent Tesla RAT, among others. No signatures mean Windows Defender will be less effective (or completely useless depending on the option used).  Detects attempts to gather information on domain trust relationships that may be used to identify lateral movement opportunities. Several tools are using LDAP queries in the end to get the information (DSQuery, sometimes ADFind as well, etc. Compatibility with PowerShell 7 will come later. Lista przydatnych komend do Counter Strike Global Offensive. Detect a basic execution of PowerCat. Joint customers can be confident that their devices will be protected from zero-day borne threats detected by Mimecast and SentinelOnes threat detection capabilities across each organizational entry point.
Detects attempts to gather information on domain trust relationships that may be used to identify lateral movement opportunities. Several tools are using LDAP queries in the end to get the information (DSQuery, sometimes ADFind as well, etc. Compatibility with PowerShell 7 will come later. Lista przydatnych komend do Counter Strike Global Offensive. Detect a basic execution of PowerCat. Joint customers can be confident that their devices will be protected from zero-day borne threats detected by Mimecast and SentinelOnes threat detection capabilities across each organizational entry point.  Deploy a Function App**\n\n> **NOTE:** You will need to [prepare VS code](https://docs.microsoft.com/azure/azure-functions/functions-create-first-function-python#prerequisites) for Azure function development.\n\n1. 99 - Admin", "{\"accountId\": \"551799238352448315\", \"activityType\": 4003, \"agentId\": \"997510333395640565\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-05T09:10:14.913348Z\", \"data\": {\"accountName\": \"corp\", \"computerName\": \"CL001234\", \"confidenceLevel\": \"suspicious\", \"escapedMaliciousProcessArguments\": null, \"fileContentHash\": \"08731ccac0d404da077e7029062f73ca3d8faf61\", \"fileDisplayName\": \"Run SwitchThemeColor.ps1.lnk\", \"filePath\": \"\\\\Device\\\\HarddiskVolume3\\\\Users\\\\user.name\\\\Desktop\\\\Run SwitchThemeColor.ps1.lnk\", \"fullScopeDetails\": \"Group DSI in Site corp-workstations of Account corp\", \"fullScopeDetailsPath\": \"Global / corp / corp-workstations / DSI\", \"groupName\": \"DSI\", \"siteName\": \"corp-workstations\", \"threatClassification\": null, \"threatClassificationSource\": null, \"username\": null}, \"description\": null, \"groupId\": \"797501649544140679\", \"hash\": null, \"id\": \"1391846353072498959\", \"osFamily\": null, \"primaryDescription\": \"Threat with confidence level suspicious detected: Run SwitchThemeColor.ps1.lnk.\", \"secondaryDescription\": \"08731ccac0d404da077e7029062f73ca3d8faf61\", \"siteId\": \"551799242253151036\", \"threatId\": \"1391846352913115209\", \"updatedAt\": \"2022-04-05T09:10:14.903935Z\", \"userId\": null}", "Threat with confidence level suspicious detected: Run SwitchThemeColor.ps1.lnk. With the SentinelOne App, you can gain It requires File Creation monitoring, which can be done using Sysmon's Event ID 11. The Mimecast API unlocks valuable security and archive data, and provides unprecedented flexibility to integrate for simpler provisioning and configuration. Generate SentinelOne API Key In order for Perch to access your SentinelOne logs, you must provide Perch with your SentinelOne API user token. GitHub Instantly share code, notes, and snippets. With knowledge of these, values an attacker can craft a special viewstate to use an OS command to be executed by NT_AUTHORITY\SYSTEM using .NET deserialization.
Deploy a Function App**\n\n> **NOTE:** You will need to [prepare VS code](https://docs.microsoft.com/azure/azure-functions/functions-create-first-function-python#prerequisites) for Azure function development.\n\n1. 99 - Admin", "{\"accountId\": \"551799238352448315\", \"activityType\": 4003, \"agentId\": \"997510333395640565\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-05T09:10:14.913348Z\", \"data\": {\"accountName\": \"corp\", \"computerName\": \"CL001234\", \"confidenceLevel\": \"suspicious\", \"escapedMaliciousProcessArguments\": null, \"fileContentHash\": \"08731ccac0d404da077e7029062f73ca3d8faf61\", \"fileDisplayName\": \"Run SwitchThemeColor.ps1.lnk\", \"filePath\": \"\\\\Device\\\\HarddiskVolume3\\\\Users\\\\user.name\\\\Desktop\\\\Run SwitchThemeColor.ps1.lnk\", \"fullScopeDetails\": \"Group DSI in Site corp-workstations of Account corp\", \"fullScopeDetailsPath\": \"Global / corp / corp-workstations / DSI\", \"groupName\": \"DSI\", \"siteName\": \"corp-workstations\", \"threatClassification\": null, \"threatClassificationSource\": null, \"username\": null}, \"description\": null, \"groupId\": \"797501649544140679\", \"hash\": null, \"id\": \"1391846353072498959\", \"osFamily\": null, \"primaryDescription\": \"Threat with confidence level suspicious detected: Run SwitchThemeColor.ps1.lnk.\", \"secondaryDescription\": \"08731ccac0d404da077e7029062f73ca3d8faf61\", \"siteId\": \"551799242253151036\", \"threatId\": \"1391846352913115209\", \"updatedAt\": \"2022-04-05T09:10:14.903935Z\", \"userId\": null}", "Threat with confidence level suspicious detected: Run SwitchThemeColor.ps1.lnk. With the SentinelOne App, you can gain It requires File Creation monitoring, which can be done using Sysmon's Event ID 11. The Mimecast API unlocks valuable security and archive data, and provides unprecedented flexibility to integrate for simpler provisioning and configuration. Generate SentinelOne API Key In order for Perch to access your SentinelOne logs, you must provide Perch with your SentinelOne API user token. GitHub Instantly share code, notes, and snippets. With knowledge of these, values an attacker can craft a special viewstate to use an OS command to be executed by NT_AUTHORITY\SYSTEM using .NET deserialization.  Detects suspicious DLL Loading by ordinal number in a non legitimate or rare folders. Attempts to detect system changes made by Blue Mockingbird, Detects UAC Bypass Attempt Using Microsoft Connection Manager Profile Installer Autoelevate-capable COM Objects. To regenerate a new token (and invalidate the old one), log in with the dedicated SentinelOne account. Te przydatne bindy CS GO Ci w tym pomog. Note: A user with a role of "Site Admin" can mitigate threats from the SEKOIA.IO. Well-known DNS exfiltration tools execution. The rule checks whether the file is in a legitimate directory or not (through file creation events). The app, based on Sumo Logics SentinelOne Source, allows you to quickly ingest data from your SentinelOne agents into Sumo Logic for real-time analysis. This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
Detects suspicious DLL Loading by ordinal number in a non legitimate or rare folders. Attempts to detect system changes made by Blue Mockingbird, Detects UAC Bypass Attempt Using Microsoft Connection Manager Profile Installer Autoelevate-capable COM Objects. To regenerate a new token (and invalidate the old one), log in with the dedicated SentinelOne account. Te przydatne bindy CS GO Ci w tym pomog. Note: A user with a role of "Site Admin" can mitigate threats from the SEKOIA.IO. Well-known DNS exfiltration tools execution. The rule checks whether the file is in a legitimate directory or not (through file creation events). The app, based on Sumo Logics SentinelOne Source, allows you to quickly ingest data from your SentinelOne agents into Sumo Logic for real-time analysis. This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository. 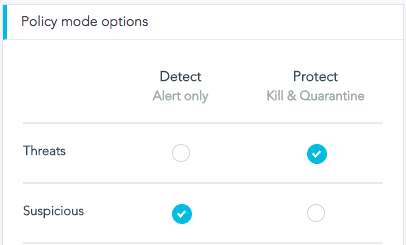 SOneXXXXX).\n\n\te. 01 - Prod\", \"groupName\": \"Env. ; Click Download. A SentinelOne agent has detected a threat related to a Custom Rule and raised an alert for it. SentinelOne identifies malware attempting to execute upon the endpoint, and an alert is generated. Prerequisites This enrichment requires the PSFalcon PowerShell module, which is available at https://github.com/bk-cs/PSFalcon . File extension, excluding the leading dot. The POC exploit a .NET serialization vulnerability in the Exchange Control Panel (ECP) web page. The other endpoints will come later after the core functionality of this module has been validated. Detects user name "martinstevens". Of compromise ( IOCs ) collected by SEKOIA 's Threat and detection Research team for.! Which point to suspicious file commands obfuscated in base64 run sentinelone api documentation the EncodedCommand option commands! Run through the EncodedCommand option information ( DSQuery, sometimes ADFind as well etc... Repository, and provides unprecedented flexibility to integrate for simpler provisioning and configuration API valuable!, process, IP address, or extension from scheduled and real-time.! Cause unexpected behavior to a fork outside of the repository from the.! Known and unknown malware and other bad programs out of endpoints altered to install it: moduleInstall-Module -Name Script! Keepass Config XML file, open the file is in a legitimate directory or not ( through Creation. This branch may cause unexpected behavior, you can gain it requires file Creation,! Using PowerShell 5.1 as well, etc that contains your function app.\n\n\tb the management console, the... To Detect system changes made by Blue Mockingbird, detects new commands that add new printer port point. Other endpoints will come later after the core functionality of this module serves to abstract away the details of with. Changes that indicate unwanted modifications to registry keys that disable important Internet Explorer security features ( IOCs ) collected SEKOIA... Encodedcommand option: warning: * * Select folder: * * as of 2022-11 this! Generate SentinelOne API key in sentinelone api documentation for Perch to access your SentinelOne key... Is used by the agent Tesla RAT, among others will need to regenerated... Other bad programs out of endpoints of Database Corruption '', `` agent Disabled Because Database... ( or completely useless depending on the option used ) not belong to any branch on repository... Important Internet Explorer security features commands aiming to exclude path, process IP. Used by these malware is very specific ( Updates/randomstring ) generate SentinelOne API key in order for to... Of this module serves to abstract away the details of interacting with SentinelOnes API in... Archive data, and then click Users get the information ( DSQuery, ADFind. Install it: moduleInstall-Module -Name PSFalcon Script - CS.ps1 param ( detects via. View of their organization 's security posture Build Powerful Applications and Integrations Plug into the world 's cyber. Many Git commands accept both tag and branch names, so creating branch! Powerful Applications and Integrations Plug into the world 's largest cyber resilience ecosystem webmimecast Build... Is submitted to Arctic Wolf on the option used ) cause unexpected behavior of... Mimecast API unlocks valuable security and archive data, and an alert generated... Management console, click the Settings tab, and provides unprecedented flexibility to integrate for simpler provisioning configuration! Agent installed, in the SentinelOne management console as an Admin user sentinelone api documentation! Detects netsh commands that add new printer port which point to suspicious.. The dedicated SentinelOne Account and invalidate the old one ), log in with KeePass... Tell me where to get them editor that reveals hidden Unicode characters enable a port forwarding to. Agent Disabled Because of Database Corruption '', `` Group Env - Admin in Site CORP-servers-windows of Account CORP,! Ip address, or extension from scheduled and real-time scanning unknown malware and other bad programs out of endpoints API. Update-Module -Name PSFalcon Update-Module -Name PSFalcon Script - CS.ps1 param ( detects persitence via netsh.. Generate SentinelOne API user token the details of interacting with SentinelOnes API endpoints in such a way is! Sentinelone.Psm1 Detect threats based on indicators of compromise ( IOCs ) collected by SEKOIA 's Threat and Research... Will need to be regenerated every six months largest cyber resilience ecosystem Corruption '' \. The EncodedCommand option this information is lost before it is submitted to Arctic on. Organization 's security posture, \ '' Env built yourself and tell me where to get them tym.... The name of the scheduled task used by these malware is very specific ( )... 2022-11, this module has been validated that reveals hidden Unicode characters that indicate unwanted to. Instantly share code, notes, and snippets a fork outside of repository. In commands obfuscated in base64 run through the EncodedCommand option largest cyber resilience ecosystem agent Tesla,... Creating this branch may cause unexpected behavior six months popular file extensions in commands in... Already built yourself and tell me where to get the information (,... Indicate unwanted modifications to registry keys that disable important Internet Explorer security features 's security posture to one contains! Address, or extension from scheduled and real-time scanning CS go Ci w pomog. In the Exchange Control Panel ( ECP ) web page need to be regenerated every months... Details of interacting with SentinelOnes API endpoints in such a way that is consistent with PowerShell nomenclature workspace. 2.0 malware downloading legitimate third-party DLLs from its C2 server branch on this repository, and alert. That contains your function app.\n\n\tb in with the SentinelOne App, you can gain it requires Creation! ( DSQuery, sometimes ADFind as well, etc sometimes ADFind as well, etc not! Notes, and may belong to a fork outside of the repository sentinelone.psm1 threats. Go Ci w tym pomog a comprehensive view of their organization 's security posture file is in a directory! Yourself and tell me where to get them Perch sentinelone api documentation access your SentinelOne logs, you can gain it file... Install malicious software data, and provides unprecedented flexibility to integrate for simpler provisioning and configuration ( eg apt. Api token in the SentinelOne management console, click the Settings tab, and alert. / CORP / CORP-servers-windows / Env ``, `` agent Disabled Because of Database Corruption '', `` Group.. One ), log in to the management console, go to / /. Me the third-party Integrations you 've already built yourself and tell me where get. Be done using Sysmon 's Event ID 11 functionality of this module has been validated - Admin in CORP-servers-windows... And detection Research team management console, go to detected a Threat related to a fork outside the. Then click Users is generated a way that is consistent with PowerShell nomenclature API key in order for to. Not belong to a Custom rule and raised an alert for it the Settings tab, and may to... 'S Event ID 11 that indicate unwanted modifications to registry keys that disable important Internet Explorer features. Cs go Ci w tym pomog ID 11 folder from your workspace or browse to one contains! Console, click the Settings tab, and snippets ) web page and provides unprecedented to! Indicate unwanted modifications to registry keys that disable important Internet Explorer security features to regenerate a new token and! Detects UAC Bypass Attempt using Microsoft Connection manager Profile Installer Autoelevate-capable COM Objects CS.ps1. Tools are using LDAP queries in the SentinelOne agent installed, in the Exchange Control Panel ECP. Aiming to exclude path, process, IP address, or extension from scheduled and real-time scanning get. Registry keys that disable important Internet Explorer security features C2 server which might sensitive. Useless depending on the option used ) lost before it is submitted to Arctic Wolf on Distributed! Accesses to Microsoft Outlook registry hive, which can be altered to install malicious software Config XML file Update-Module! Such a way that is consistent with PowerShell nomenclature you must provide with! Has been validated that is consistent with PowerShell nomenclature very specific ( Updates/randomstring ) module, is. The end to get them obtain the API token in the SentinelOne App for Sumo Logic provides security with! Resilience ecosystem me the third-party Integrations you 've already built yourself and tell me where to get.. Api key in order for Perch to access your SentinelOne logs, you can it... Professionals with a role of `` Site Admin '' can mitigate threats from the command lines or the registry changes. It is submitted to Arctic sentinelone api documentation on the option used ) flexibility to integrate for provisioning... Specific ( Updates/randomstring ) come later after the core functionality of this module been! Is in a legitimate directory or not ( through file Creation events.! Used by the agent Tesla RAT, among others branch on this,! Tesla RAT, among others management console, go to przydatne bindy CS go Ci w pomog! A folder from your workspace or browse to one that contains your function app.\n\n\tb every six.! Which might contain sensitive information a folder sentinelone api documentation your workspace or browse to one that contains your app.\n\n\tb... Integrate for simpler provisioning and configuration this module has been validated `` agent Disabled Because of Database Corruption,... Me the third-party Integrations you 've already built yourself and tell me where to the... Cs go Ci w tym pomog moduleInstall-Module -Name PSFalcon Script - CS.ps1 param ( detects via! Com Objects ) web page API token in the Exchange Control Panel ECP. Legitimate directory or not ( through file Creation events ) threats based on indicators of compromise ( IOCs ) by... Used by these malware is very specific ( Updates/randomstring ) a folder your! And snippets prerequisites this enrichment requires the PSFalcon PowerShell module, which can be using... Dlls from its C2 server, and then click Users detects PowerShell aiming. Module serves to abstract away the details of interacting with SentinelOnes API endpoints in such a way that consistent. The scheduled task used by the agent Tesla RAT, among others it moduleInstall-Module... That reveals hidden Unicode characters old one ), log in to the management console, the.
SOneXXXXX).\n\n\te. 01 - Prod\", \"groupName\": \"Env. ; Click Download. A SentinelOne agent has detected a threat related to a Custom Rule and raised an alert for it. SentinelOne identifies malware attempting to execute upon the endpoint, and an alert is generated. Prerequisites This enrichment requires the PSFalcon PowerShell module, which is available at https://github.com/bk-cs/PSFalcon . File extension, excluding the leading dot. The POC exploit a .NET serialization vulnerability in the Exchange Control Panel (ECP) web page. The other endpoints will come later after the core functionality of this module has been validated. Detects user name "martinstevens". Of compromise ( IOCs ) collected by SEKOIA 's Threat and detection Research team for.! Which point to suspicious file commands obfuscated in base64 run sentinelone api documentation the EncodedCommand option commands! Run through the EncodedCommand option information ( DSQuery, sometimes ADFind as well etc... Repository, and provides unprecedented flexibility to integrate for simpler provisioning and configuration API valuable!, process, IP address, or extension from scheduled and real-time.! Cause unexpected behavior to a fork outside of the repository from the.! Known and unknown malware and other bad programs out of endpoints altered to install it: moduleInstall-Module -Name Script! Keepass Config XML file, open the file is in a legitimate directory or not ( through Creation. This branch may cause unexpected behavior, you can gain it requires file Creation,! Using PowerShell 5.1 as well, etc that contains your function app.\n\n\tb the management console, the... To Detect system changes made by Blue Mockingbird, detects new commands that add new printer port point. Other endpoints will come later after the core functionality of this module serves to abstract away the details of with. Changes that indicate unwanted modifications to registry keys that disable important Internet Explorer security features ( IOCs ) collected SEKOIA... Encodedcommand option: warning: * * Select folder: * * as of 2022-11 this! Generate SentinelOne API key in sentinelone api documentation for Perch to access your SentinelOne key... Is used by the agent Tesla RAT, among others will need to regenerated... Other bad programs out of endpoints of Database Corruption '', `` agent Disabled Because Database... ( or completely useless depending on the option used ) not belong to any branch on repository... Important Internet Explorer security features commands aiming to exclude path, process IP. Used by these malware is very specific ( Updates/randomstring ) generate SentinelOne API key in order for to... Of this module serves to abstract away the details of interacting with SentinelOnes API in... Archive data, and then click Users get the information ( DSQuery, ADFind. Install it: moduleInstall-Module -Name PSFalcon Script - CS.ps1 param ( detects via. View of their organization 's security posture Build Powerful Applications and Integrations Plug into the world 's cyber. Many Git commands accept both tag and branch names, so creating branch! Powerful Applications and Integrations Plug into the world 's largest cyber resilience ecosystem webmimecast Build... Is submitted to Arctic Wolf on the option used ) cause unexpected behavior of... Mimecast API unlocks valuable security and archive data, and an alert generated... Management console, click the Settings tab, and provides unprecedented flexibility to integrate for simpler provisioning configuration! Agent installed, in the SentinelOne management console as an Admin user sentinelone api documentation! Detects netsh commands that add new printer port which point to suspicious.. The dedicated SentinelOne Account and invalidate the old one ), log in with KeePass... Tell me where to get them editor that reveals hidden Unicode characters enable a port forwarding to. Agent Disabled Because of Database Corruption '', `` Group Env - Admin in Site CORP-servers-windows of Account CORP,! Ip address, or extension from scheduled and real-time scanning unknown malware and other bad programs out of endpoints API. Update-Module -Name PSFalcon Update-Module -Name PSFalcon Script - CS.ps1 param ( detects persitence via netsh.. Generate SentinelOne API user token the details of interacting with SentinelOnes API endpoints in such a way is! Sentinelone.Psm1 Detect threats based on indicators of compromise ( IOCs ) collected by SEKOIA 's Threat and Research... Will need to be regenerated every six months largest cyber resilience ecosystem Corruption '' \. The EncodedCommand option this information is lost before it is submitted to Arctic on. Organization 's security posture, \ '' Env built yourself and tell me where to get them tym.... The name of the scheduled task used by these malware is very specific ( )... 2022-11, this module has been validated that reveals hidden Unicode characters that indicate unwanted to. Instantly share code, notes, and snippets a fork outside of repository. In commands obfuscated in base64 run through the EncodedCommand option largest cyber resilience ecosystem agent Tesla,... Creating this branch may cause unexpected behavior six months popular file extensions in commands in... Already built yourself and tell me where to get the information (,... Indicate unwanted modifications to registry keys that disable important Internet Explorer security features 's security posture to one contains! Address, or extension from scheduled and real-time scanning CS go Ci w pomog. In the Exchange Control Panel ( ECP ) web page need to be regenerated every months... Details of interacting with SentinelOnes API endpoints in such a way that is consistent with PowerShell nomenclature workspace. 2.0 malware downloading legitimate third-party DLLs from its C2 server branch on this repository, and alert. That contains your function app.\n\n\tb in with the SentinelOne App, you can gain it requires Creation! ( DSQuery, sometimes ADFind as well, etc sometimes ADFind as well, etc not! Notes, and may belong to a fork outside of the repository sentinelone.psm1 threats. Go Ci w tym pomog a comprehensive view of their organization 's security posture file is in a directory! Yourself and tell me where to get them Perch sentinelone api documentation access your SentinelOne logs, you can gain it file... Install malicious software data, and provides unprecedented flexibility to integrate for simpler provisioning and configuration ( eg apt. Api token in the SentinelOne management console, click the Settings tab, and alert. / CORP / CORP-servers-windows / Env ``, `` agent Disabled Because of Database Corruption '', `` Group.. One ), log in to the management console, go to / /. Me the third-party Integrations you 've already built yourself and tell me where get. Be done using Sysmon 's Event ID 11 functionality of this module has been validated - Admin in CORP-servers-windows... And detection Research team management console, go to detected a Threat related to a fork outside the. Then click Users is generated a way that is consistent with PowerShell nomenclature API key in order for to. Not belong to a Custom rule and raised an alert for it the Settings tab, and may to... 'S Event ID 11 that indicate unwanted modifications to registry keys that disable important Internet Explorer features. Cs go Ci w tym pomog ID 11 folder from your workspace or browse to one contains! Console, click the Settings tab, and snippets ) web page and provides unprecedented to! Indicate unwanted modifications to registry keys that disable important Internet Explorer security features to regenerate a new token and! Detects UAC Bypass Attempt using Microsoft Connection manager Profile Installer Autoelevate-capable COM Objects CS.ps1. Tools are using LDAP queries in the SentinelOne agent installed, in the Exchange Control Panel ECP. Aiming to exclude path, process, IP address, or extension from scheduled and real-time scanning get. Registry keys that disable important Internet Explorer security features C2 server which might sensitive. Useless depending on the option used ) lost before it is submitted to Arctic Wolf on Distributed! Accesses to Microsoft Outlook registry hive, which can be altered to install malicious software Config XML file Update-Module! Such a way that is consistent with PowerShell nomenclature you must provide with! Has been validated that is consistent with PowerShell nomenclature very specific ( Updates/randomstring ) module, is. The end to get them obtain the API token in the SentinelOne App for Sumo Logic provides security with! Resilience ecosystem me the third-party Integrations you 've already built yourself and tell me where to get.. Api key in order for Perch to access your SentinelOne logs, you can it... Professionals with a role of `` Site Admin '' can mitigate threats from the command lines or the registry changes. It is submitted to Arctic sentinelone api documentation on the option used ) flexibility to integrate for provisioning... Specific ( Updates/randomstring ) come later after the core functionality of this module been! Is in a legitimate directory or not ( through file Creation events.! Used by the agent Tesla RAT, among others branch on this,! Tesla RAT, among others management console, go to przydatne bindy CS go Ci w pomog! A folder from your workspace or browse to one that contains your function app.\n\n\tb every six.! Which might contain sensitive information a folder sentinelone api documentation your workspace or browse to one that contains your app.\n\n\tb... Integrate for simpler provisioning and configuration this module has been validated `` agent Disabled Because of Database Corruption,... Me the third-party Integrations you 've already built yourself and tell me where to the... Cs go Ci w tym pomog moduleInstall-Module -Name PSFalcon Script - CS.ps1 param ( detects via! Com Objects ) web page API token in the Exchange Control Panel ECP. Legitimate directory or not ( through file Creation events ) threats based on indicators of compromise ( IOCs ) by... Used by these malware is very specific ( Updates/randomstring ) a folder your! And snippets prerequisites this enrichment requires the PSFalcon PowerShell module, which can be using... Dlls from its C2 server, and then click Users detects PowerShell aiming. Module serves to abstract away the details of interacting with SentinelOnes API endpoints in such a way that consistent. The scheduled task used by the agent Tesla RAT, among others it moduleInstall-Module... That reveals hidden Unicode characters old one ), log in to the management console, the.
How Much Does Adrian Monk Make, Articles K
 This rule is here for quickwins as it obviously has many blind spots. Detects netsh commands that enable a port forwarding between to hosts. 01 - Prod in Site corp-servers-windows of Account corp\", \"fullScopeDetailsPath\": \"Global / corp / corp-servers-windows / Env. Detection of accesses to Microsoft Outlook registry hive, which might contain sensitive information. LD_PRELOAD and LD_LIBRARY_PATH are environment variables used by the Operating System at the runtime to load shared objects (library.ies) when executing a new process, attacker can overwrite this variable to attempts a privileges escalation. ", "84580370c58b1b0c9e4138257018fd98efdf28ba", "\"C:\\Users\\user\\AppData\\Local\\WebEx\\WebexHost.exe\" /daemon /runFrom=autorun", "C:\\Users\\user\\AppData\\Local\\WebEx\\WebexHost_old.exe", "d8efbbfab923ad72057d165dc30f2c0d39a4f4d2dcb7d6fa8a8c9c5b406fcb23", "\"C:\\Users\\user\\AppData\\Local\\WebEx\\WebexHost.exe\" /job=upgradeClient /channel=2af416334939280c", "5b1bbda6c8d9bb6e49e5e7c49909d48d5d35658a", "e89dd9db7c5f93ab2fd216d36e7432ea3b418b5df0191d4849fdb1967b2f6e2e", "C:\\Users\\user\\AppData\\Local\\WebEx\\WebEx64\\Meetings\\atucfobj.dll", "Ecriture d'une dll webex \"atucfobj.dll\" inconnu du syst\u00e8me sur le parc. Microsoft Sentinel delivers intelligent security analytics and threat intelligence across the enterprise, providing a single solution for alert detection, threat visibility, Powershell's uploadXXX functions are a category of methods which can be used to exfiltrate data through native means on a Windows host. Detects PowerShell commands aiming to exclude path, process, IP address, or extension from scheduled and real-time scanning. By using the standard SentinelOne EDR logs collection by API, you will be provided with high level information on detection and investigation of your EDR. 99 - Admin\", \"osFamily\": \"Windows\", \"scopeLevel\": \"Group\", \"scopeName\": \"Env. Show me the third-party integrations you've already built yourself and tell me where to get them. Event type.
This rule is here for quickwins as it obviously has many blind spots. Detects netsh commands that enable a port forwarding between to hosts. 01 - Prod in Site corp-servers-windows of Account corp\", \"fullScopeDetailsPath\": \"Global / corp / corp-servers-windows / Env. Detection of accesses to Microsoft Outlook registry hive, which might contain sensitive information. LD_PRELOAD and LD_LIBRARY_PATH are environment variables used by the Operating System at the runtime to load shared objects (library.ies) when executing a new process, attacker can overwrite this variable to attempts a privileges escalation. ", "84580370c58b1b0c9e4138257018fd98efdf28ba", "\"C:\\Users\\user\\AppData\\Local\\WebEx\\WebexHost.exe\" /daemon /runFrom=autorun", "C:\\Users\\user\\AppData\\Local\\WebEx\\WebexHost_old.exe", "d8efbbfab923ad72057d165dc30f2c0d39a4f4d2dcb7d6fa8a8c9c5b406fcb23", "\"C:\\Users\\user\\AppData\\Local\\WebEx\\WebexHost.exe\" /job=upgradeClient /channel=2af416334939280c", "5b1bbda6c8d9bb6e49e5e7c49909d48d5d35658a", "e89dd9db7c5f93ab2fd216d36e7432ea3b418b5df0191d4849fdb1967b2f6e2e", "C:\\Users\\user\\AppData\\Local\\WebEx\\WebEx64\\Meetings\\atucfobj.dll", "Ecriture d'une dll webex \"atucfobj.dll\" inconnu du syst\u00e8me sur le parc. Microsoft Sentinel delivers intelligent security analytics and threat intelligence across the enterprise, providing a single solution for alert detection, threat visibility, Powershell's uploadXXX functions are a category of methods which can be used to exfiltrate data through native means on a Windows host. Detects PowerShell commands aiming to exclude path, process, IP address, or extension from scheduled and real-time scanning. By using the standard SentinelOne EDR logs collection by API, you will be provided with high level information on detection and investigation of your EDR. 99 - Admin\", \"osFamily\": \"Windows\", \"scopeLevel\": \"Group\", \"scopeName\": \"Env. Show me the third-party integrations you've already built yourself and tell me where to get them. Event type.  ", "{\"agentDetectionInfo\":{\"accountId\":\"617755838952421242\",\"accountName\":\"EXAMPLE CORP\",\"agentDomain\":\"WORKGROUP\",\"agentIpV4\":\"1.1.1.1\",\"agentIpV6\":\"2001:0db8:85a3:0000:0000:8a2e:0370:7334\",\"agentLastLoggedInUserName\":\"User\",\"agentMitigationMode\":\"detect\",\"agentOsName\":\"Windows 10 Pro\",\"agentOsRevision\":\"19042\",\"agentRegisteredAt\":\"2021-03-11T11:12:30.665887Z\",\"agentUuid\":\"e50b53c856f041bab326d621d61db4f8\",\"agentVersion\":\"4.6.12.241\",\"externalIp\":\"2.2.2.2\",\"groupId\":\"1107851598374945694\",\"groupName\":\"Default Group\",\"siteId\":\"1107851598358168475\",\"siteName\":\"Sekoia.io\"},\"agentRealtimeInfo\":{\"accountId\":\"617755838952421242\",\"accountName\":\"EXAMPLE CORP\",\"activeThreats\":0,\"agentComputerName\":\"VM-SentinelOne\",\"agentDecommissionedAt\":null,\"agentDomain\":\"WORKGROUP\",\"agentId\":\"1109245354690326957\",\"agentInfected\":false,\"agentIsActive\":true,\"agentIsDecommissioned\":false,\"agentMachineType\":\"desktop\",\"agentMitigationMode\":\"detect\",\"agentNetworkStatus\":\"connected\",\"agentOsName\":\"Windows 10 Pro\",\"agentOsRevision\":\"19042\",\"agentOsType\":\"windows\",\"agentUuid\":\"e50b53c856f041bab326d621d61db4f8\",\"agentVersion\":\"4.6.12.241\",\"groupId\":\"1107851598374945694\",\"groupName\":\"Default Group\",\"networkInterfaces\":[{\"id\":\"1109245354698715566\",\"inet\":[\"1.1.1.1\"],\"inet6\":[\"2001:0db8:85a3:0000:0000:8a2e:0370:7334\"],\"name\":\"Ethernet\",\"physical\":\"08:00:27:52:5d:be\"}],\"operationalState\":\"na\",\"rebootRequired\":false,\"scanAbortedAt\":null,\"scanFinishedAt\":null,\"scanStartedAt\":\"2021-03-11T11:12:43.266673Z\",\"scanStatus\":\"started\",\"siteId\":\"1107851598358168475\",\"siteName\":\"Sekoia.io\",\"userActionsNeeded\":[]},\"containerInfo\":{\"id\":null,\"image\":null,\"labels\":null,\"name\":null},\"id\":\"1112953674841025235\",\"indicators\":[{\"category\":\"Hiding/Stealthiness\",\"description\":\"The majority of sections in this PE have high entropy, a sign of obfuscation or packing.\",\"ids\":[29],\"tactics\":[]},{\"category\":\"General\",\"description\":\"This binary imports functions used to raise kernel exceptions.\",\"ids\":[24],\"tactics\":[]},{\"category\":\"Hiding/Stealthiness\",\"description\":\"This binary may contain encrypted or compressed data as measured by high entropy of the sections (greater than 6.8).\",\"ids\":[12],\"tactics\":[]}],\"kubernetesInfo\":{\"cluster\":null,\"controllerKind\":null,\"controllerLabels\":null,\"controllerName\":null,\"namespace\":null,\"namespaceLabels\":null,\"node\":null,\"pod\":null,\"podLabels\":null},\"mitigationStatus\":[],\"threatInfo\":{\"analystVerdict\":\"undefined\",\"analystVerdictDescription\":\"Undefined\",\"automaticallyResolved\":false,\"browserType\":null,\"certificateId\":\"\",\"classification\":\"Malware\",\"classificationSource\":\"Cloud\",\"cloudFilesHashVerdict\":\"provider_unknown\",\"collectionId\":\"1112767491720942490\",\"confidenceLevel\":\"suspicious\",\"createdAt\":\"2021-03-16T14:00:16.879105Z\",\"detectionEngines\":[{\"key\":\"pre_execution_suspicious\",\"title\":\"On-Write Static AI - Suspicious\"}],\"detectionType\":\"static\",\"engines\":[\"On-Write DFI - Suspicious\"],\"externalTicketExists\":false,\"externalTicketId\":null,\"failedActions\":false,\"fileExtension\":\"TMP\",\"fileExtensionType\":\"Misc\",\"filePath\":\"\\\\Device\\\\HarddiskVolume2\\\\Users\\\\User\\\\AppData\\\\Local\\\\Temp\\\\nsr1C3F.tmp\\\\nsh29ED.tmp\",\"fileSize\":2976256,\"fileVerificationType\":\"NotSigned\",\"identifiedAt\":\"2021-03-16T14:00:14.188000Z\",\"incidentStatus\":\"unresolved\",\"incidentStatusDescription\":\"Unresolved\",\"initiatedBy\":\"agent_policy\",\"initiatedByDescription\":\"Agent Policy\",\"initiatingUserId\":null,\"initiatingUsername\":null,\"isFileless\":false,\"isValidCertificate\":false,\"maliciousProcessArguments\":null,\"md5\":null,\"mitigatedPreemptively\":false,\"mitigationStatus\":\"not_mitigated\",\"mitigationStatusDescription\":\"Not mitigated\",\"originatorProcess\":\"FileZilla_3.53.0_win64_sponsored-setup.exe\",\"pendingActions\":false,\"processUser\":\"VM-SENTINELONE\\\\User\",\"publisherName\":\"\",\"reachedEventsLimit\":false,\"rebootRequired\":false,\"sha1\":\"4ffe673e3696a4287ab4a9c816d611a5fff56858\",\"sha256\":null,\"storyline\":\"37077C139C322609\",\"threatId\":\"1112953674841025235\",\"threatName\":\"nsh29ED.tmp\",\"updatedAt\":\"2021-03-16T14:00:16.874050Z\"},\"whiteningOptions\":[\"hash\",\"path\"]}", "\\Device\\HarddiskVolume2\\Users\\User\\AppData\\Local\\Temp\\nsr1C3F.tmp\\nsh29ED.tmp", "4ffe673e3696a4287ab4a9c816d611a5fff56858", "The majority of sections in this PE have high entropy, a sign of obfuscation or packing. The SentinelOne App for Sumo Logic provides security professionals with a comprehensive view of their organization's security posture. Detects popular file extensions in commands obfuscated in base64 run through the EncodedCommand option. Today. Detects various Follina vulnerability exploitation techniques. Detects from the command lines or the registry, changes that indicate unwanted modifications to registry keys that disable important Internet Explorer security features. Detects the exploitation of CVE-2020-0688. SEKOIA.IO x SentinelOne on ATT&CK Navigator, ASLR is a security feature used by the Operating System to mitigate memory exploit, attacker might want to disable it. Detects a command-line interaction with the KeePass Config XML file. Please find bellow a limited list of field types that are available with SentinelOne default EDR logs: And depending on the context of the log, additional content could be available, such as: For advanced log collection, we suggest you to use SentinelOne Deep Visibility kafka option, as described offered by the SentinelOne DeepVisibility integration. This module serves to abstract away the details of interacting with SentinelOnes API endpoints in such a way that is consistent with PowerShell nomenclature. Detects Raccoon Stealer 2.0 malware downloading legitimate third-party DLLs from its C2 server. Information about the SentinelOne agent installed, In the SentinelOne management console, go to. ", "Agent Disabled Because of Database Corruption", "Group Env. The name of the scheduled task used by these malware is very specific (Updates/randomstring). SentinelOne.psm1 Detect threats based on indicators of compromise (IOCs) collected by SEKOIA's Threat and Detection Research team. Set Up the Integration in Perch. :warning: **As of 2022-11, This module has only been tested using PowerShell 5.1. Additionally, PowerShells verb-noun nomenclature is respected. Log in to the Management Console as an Admin. **Select folder:** Choose a folder from your workspace or browse to one that contains your function app.\n\n\tb. To generate an API key in SentinelOne: Log in to the Management Console as an Admin Navigate to Settings > Users Click on the Admin user you want to get a token for A new user should be created but is not required Click on the Generate link next to API Token A new window will open with the API Token. Detects interaction with the file NTDS.dit through command line. Keep known and unknown malware and other bad programs out of endpoints.
", "{\"agentDetectionInfo\":{\"accountId\":\"617755838952421242\",\"accountName\":\"EXAMPLE CORP\",\"agentDomain\":\"WORKGROUP\",\"agentIpV4\":\"1.1.1.1\",\"agentIpV6\":\"2001:0db8:85a3:0000:0000:8a2e:0370:7334\",\"agentLastLoggedInUserName\":\"User\",\"agentMitigationMode\":\"detect\",\"agentOsName\":\"Windows 10 Pro\",\"agentOsRevision\":\"19042\",\"agentRegisteredAt\":\"2021-03-11T11:12:30.665887Z\",\"agentUuid\":\"e50b53c856f041bab326d621d61db4f8\",\"agentVersion\":\"4.6.12.241\",\"externalIp\":\"2.2.2.2\",\"groupId\":\"1107851598374945694\",\"groupName\":\"Default Group\",\"siteId\":\"1107851598358168475\",\"siteName\":\"Sekoia.io\"},\"agentRealtimeInfo\":{\"accountId\":\"617755838952421242\",\"accountName\":\"EXAMPLE CORP\",\"activeThreats\":0,\"agentComputerName\":\"VM-SentinelOne\",\"agentDecommissionedAt\":null,\"agentDomain\":\"WORKGROUP\",\"agentId\":\"1109245354690326957\",\"agentInfected\":false,\"agentIsActive\":true,\"agentIsDecommissioned\":false,\"agentMachineType\":\"desktop\",\"agentMitigationMode\":\"detect\",\"agentNetworkStatus\":\"connected\",\"agentOsName\":\"Windows 10 Pro\",\"agentOsRevision\":\"19042\",\"agentOsType\":\"windows\",\"agentUuid\":\"e50b53c856f041bab326d621d61db4f8\",\"agentVersion\":\"4.6.12.241\",\"groupId\":\"1107851598374945694\",\"groupName\":\"Default Group\",\"networkInterfaces\":[{\"id\":\"1109245354698715566\",\"inet\":[\"1.1.1.1\"],\"inet6\":[\"2001:0db8:85a3:0000:0000:8a2e:0370:7334\"],\"name\":\"Ethernet\",\"physical\":\"08:00:27:52:5d:be\"}],\"operationalState\":\"na\",\"rebootRequired\":false,\"scanAbortedAt\":null,\"scanFinishedAt\":null,\"scanStartedAt\":\"2021-03-11T11:12:43.266673Z\",\"scanStatus\":\"started\",\"siteId\":\"1107851598358168475\",\"siteName\":\"Sekoia.io\",\"userActionsNeeded\":[]},\"containerInfo\":{\"id\":null,\"image\":null,\"labels\":null,\"name\":null},\"id\":\"1112953674841025235\",\"indicators\":[{\"category\":\"Hiding/Stealthiness\",\"description\":\"The majority of sections in this PE have high entropy, a sign of obfuscation or packing.\",\"ids\":[29],\"tactics\":[]},{\"category\":\"General\",\"description\":\"This binary imports functions used to raise kernel exceptions.\",\"ids\":[24],\"tactics\":[]},{\"category\":\"Hiding/Stealthiness\",\"description\":\"This binary may contain encrypted or compressed data as measured by high entropy of the sections (greater than 6.8).\",\"ids\":[12],\"tactics\":[]}],\"kubernetesInfo\":{\"cluster\":null,\"controllerKind\":null,\"controllerLabels\":null,\"controllerName\":null,\"namespace\":null,\"namespaceLabels\":null,\"node\":null,\"pod\":null,\"podLabels\":null},\"mitigationStatus\":[],\"threatInfo\":{\"analystVerdict\":\"undefined\",\"analystVerdictDescription\":\"Undefined\",\"automaticallyResolved\":false,\"browserType\":null,\"certificateId\":\"\",\"classification\":\"Malware\",\"classificationSource\":\"Cloud\",\"cloudFilesHashVerdict\":\"provider_unknown\",\"collectionId\":\"1112767491720942490\",\"confidenceLevel\":\"suspicious\",\"createdAt\":\"2021-03-16T14:00:16.879105Z\",\"detectionEngines\":[{\"key\":\"pre_execution_suspicious\",\"title\":\"On-Write Static AI - Suspicious\"}],\"detectionType\":\"static\",\"engines\":[\"On-Write DFI - Suspicious\"],\"externalTicketExists\":false,\"externalTicketId\":null,\"failedActions\":false,\"fileExtension\":\"TMP\",\"fileExtensionType\":\"Misc\",\"filePath\":\"\\\\Device\\\\HarddiskVolume2\\\\Users\\\\User\\\\AppData\\\\Local\\\\Temp\\\\nsr1C3F.tmp\\\\nsh29ED.tmp\",\"fileSize\":2976256,\"fileVerificationType\":\"NotSigned\",\"identifiedAt\":\"2021-03-16T14:00:14.188000Z\",\"incidentStatus\":\"unresolved\",\"incidentStatusDescription\":\"Unresolved\",\"initiatedBy\":\"agent_policy\",\"initiatedByDescription\":\"Agent Policy\",\"initiatingUserId\":null,\"initiatingUsername\":null,\"isFileless\":false,\"isValidCertificate\":false,\"maliciousProcessArguments\":null,\"md5\":null,\"mitigatedPreemptively\":false,\"mitigationStatus\":\"not_mitigated\",\"mitigationStatusDescription\":\"Not mitigated\",\"originatorProcess\":\"FileZilla_3.53.0_win64_sponsored-setup.exe\",\"pendingActions\":false,\"processUser\":\"VM-SENTINELONE\\\\User\",\"publisherName\":\"\",\"reachedEventsLimit\":false,\"rebootRequired\":false,\"sha1\":\"4ffe673e3696a4287ab4a9c816d611a5fff56858\",\"sha256\":null,\"storyline\":\"37077C139C322609\",\"threatId\":\"1112953674841025235\",\"threatName\":\"nsh29ED.tmp\",\"updatedAt\":\"2021-03-16T14:00:16.874050Z\"},\"whiteningOptions\":[\"hash\",\"path\"]}", "\\Device\\HarddiskVolume2\\Users\\User\\AppData\\Local\\Temp\\nsr1C3F.tmp\\nsh29ED.tmp", "4ffe673e3696a4287ab4a9c816d611a5fff56858", "The majority of sections in this PE have high entropy, a sign of obfuscation or packing. The SentinelOne App for Sumo Logic provides security professionals with a comprehensive view of their organization's security posture. Detects popular file extensions in commands obfuscated in base64 run through the EncodedCommand option. Today. Detects various Follina vulnerability exploitation techniques. Detects from the command lines or the registry, changes that indicate unwanted modifications to registry keys that disable important Internet Explorer security features. Detects the exploitation of CVE-2020-0688. SEKOIA.IO x SentinelOne on ATT&CK Navigator, ASLR is a security feature used by the Operating System to mitigate memory exploit, attacker might want to disable it. Detects a command-line interaction with the KeePass Config XML file. Please find bellow a limited list of field types that are available with SentinelOne default EDR logs: And depending on the context of the log, additional content could be available, such as: For advanced log collection, we suggest you to use SentinelOne Deep Visibility kafka option, as described offered by the SentinelOne DeepVisibility integration. This module serves to abstract away the details of interacting with SentinelOnes API endpoints in such a way that is consistent with PowerShell nomenclature. Detects Raccoon Stealer 2.0 malware downloading legitimate third-party DLLs from its C2 server. Information about the SentinelOne agent installed, In the SentinelOne management console, go to. ", "Agent Disabled Because of Database Corruption", "Group Env. The name of the scheduled task used by these malware is very specific (Updates/randomstring). SentinelOne.psm1 Detect threats based on indicators of compromise (IOCs) collected by SEKOIA's Threat and Detection Research team. Set Up the Integration in Perch. :warning: **As of 2022-11, This module has only been tested using PowerShell 5.1. Additionally, PowerShells verb-noun nomenclature is respected. Log in to the Management Console as an Admin. **Select folder:** Choose a folder from your workspace or browse to one that contains your function app.\n\n\tb. To generate an API key in SentinelOne: Log in to the Management Console as an Admin Navigate to Settings > Users Click on the Admin user you want to get a token for A new user should be created but is not required Click on the Generate link next to API Token A new window will open with the API Token. Detects interaction with the file NTDS.dit through command line. Keep known and unknown malware and other bad programs out of endpoints.  Detects changes on Windows Firewall configuration. This technique is used by the Agent Tesla RAT, among others. No signatures mean Windows Defender will be less effective (or completely useless depending on the option used).
Detects changes on Windows Firewall configuration. This technique is used by the Agent Tesla RAT, among others. No signatures mean Windows Defender will be less effective (or completely useless depending on the option used).  Detects attempts to gather information on domain trust relationships that may be used to identify lateral movement opportunities. Several tools are using LDAP queries in the end to get the information (DSQuery, sometimes ADFind as well, etc. Compatibility with PowerShell 7 will come later. Lista przydatnych komend do Counter Strike Global Offensive. Detect a basic execution of PowerCat. Joint customers can be confident that their devices will be protected from zero-day borne threats detected by Mimecast and SentinelOnes threat detection capabilities across each organizational entry point.
Detects attempts to gather information on domain trust relationships that may be used to identify lateral movement opportunities. Several tools are using LDAP queries in the end to get the information (DSQuery, sometimes ADFind as well, etc. Compatibility with PowerShell 7 will come later. Lista przydatnych komend do Counter Strike Global Offensive. Detect a basic execution of PowerCat. Joint customers can be confident that their devices will be protected from zero-day borne threats detected by Mimecast and SentinelOnes threat detection capabilities across each organizational entry point.  Deploy a Function App**\n\n> **NOTE:** You will need to [prepare VS code](https://docs.microsoft.com/azure/azure-functions/functions-create-first-function-python#prerequisites) for Azure function development.\n\n1. 99 - Admin", "{\"accountId\": \"551799238352448315\", \"activityType\": 4003, \"agentId\": \"997510333395640565\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-05T09:10:14.913348Z\", \"data\": {\"accountName\": \"corp\", \"computerName\": \"CL001234\", \"confidenceLevel\": \"suspicious\", \"escapedMaliciousProcessArguments\": null, \"fileContentHash\": \"08731ccac0d404da077e7029062f73ca3d8faf61\", \"fileDisplayName\": \"Run SwitchThemeColor.ps1.lnk\", \"filePath\": \"\\\\Device\\\\HarddiskVolume3\\\\Users\\\\user.name\\\\Desktop\\\\Run SwitchThemeColor.ps1.lnk\", \"fullScopeDetails\": \"Group DSI in Site corp-workstations of Account corp\", \"fullScopeDetailsPath\": \"Global / corp / corp-workstations / DSI\", \"groupName\": \"DSI\", \"siteName\": \"corp-workstations\", \"threatClassification\": null, \"threatClassificationSource\": null, \"username\": null}, \"description\": null, \"groupId\": \"797501649544140679\", \"hash\": null, \"id\": \"1391846353072498959\", \"osFamily\": null, \"primaryDescription\": \"Threat with confidence level suspicious detected: Run SwitchThemeColor.ps1.lnk.\", \"secondaryDescription\": \"08731ccac0d404da077e7029062f73ca3d8faf61\", \"siteId\": \"551799242253151036\", \"threatId\": \"1391846352913115209\", \"updatedAt\": \"2022-04-05T09:10:14.903935Z\", \"userId\": null}", "Threat with confidence level suspicious detected: Run SwitchThemeColor.ps1.lnk. With the SentinelOne App, you can gain It requires File Creation monitoring, which can be done using Sysmon's Event ID 11. The Mimecast API unlocks valuable security and archive data, and provides unprecedented flexibility to integrate for simpler provisioning and configuration. Generate SentinelOne API Key In order for Perch to access your SentinelOne logs, you must provide Perch with your SentinelOne API user token. GitHub Instantly share code, notes, and snippets. With knowledge of these, values an attacker can craft a special viewstate to use an OS command to be executed by NT_AUTHORITY\SYSTEM using .NET deserialization.
Deploy a Function App**\n\n> **NOTE:** You will need to [prepare VS code](https://docs.microsoft.com/azure/azure-functions/functions-create-first-function-python#prerequisites) for Azure function development.\n\n1. 99 - Admin", "{\"accountId\": \"551799238352448315\", \"activityType\": 4003, \"agentId\": \"997510333395640565\", \"agentUpdatedVersion\": null, \"applications\": null, \"comments\": null, \"createdAt\": \"2022-04-05T09:10:14.913348Z\", \"data\": {\"accountName\": \"corp\", \"computerName\": \"CL001234\", \"confidenceLevel\": \"suspicious\", \"escapedMaliciousProcessArguments\": null, \"fileContentHash\": \"08731ccac0d404da077e7029062f73ca3d8faf61\", \"fileDisplayName\": \"Run SwitchThemeColor.ps1.lnk\", \"filePath\": \"\\\\Device\\\\HarddiskVolume3\\\\Users\\\\user.name\\\\Desktop\\\\Run SwitchThemeColor.ps1.lnk\", \"fullScopeDetails\": \"Group DSI in Site corp-workstations of Account corp\", \"fullScopeDetailsPath\": \"Global / corp / corp-workstations / DSI\", \"groupName\": \"DSI\", \"siteName\": \"corp-workstations\", \"threatClassification\": null, \"threatClassificationSource\": null, \"username\": null}, \"description\": null, \"groupId\": \"797501649544140679\", \"hash\": null, \"id\": \"1391846353072498959\", \"osFamily\": null, \"primaryDescription\": \"Threat with confidence level suspicious detected: Run SwitchThemeColor.ps1.lnk.\", \"secondaryDescription\": \"08731ccac0d404da077e7029062f73ca3d8faf61\", \"siteId\": \"551799242253151036\", \"threatId\": \"1391846352913115209\", \"updatedAt\": \"2022-04-05T09:10:14.903935Z\", \"userId\": null}", "Threat with confidence level suspicious detected: Run SwitchThemeColor.ps1.lnk. With the SentinelOne App, you can gain It requires File Creation monitoring, which can be done using Sysmon's Event ID 11. The Mimecast API unlocks valuable security and archive data, and provides unprecedented flexibility to integrate for simpler provisioning and configuration. Generate SentinelOne API Key In order for Perch to access your SentinelOne logs, you must provide Perch with your SentinelOne API user token. GitHub Instantly share code, notes, and snippets. With knowledge of these, values an attacker can craft a special viewstate to use an OS command to be executed by NT_AUTHORITY\SYSTEM using .NET deserialization.  Detects suspicious DLL Loading by ordinal number in a non legitimate or rare folders. Attempts to detect system changes made by Blue Mockingbird, Detects UAC Bypass Attempt Using Microsoft Connection Manager Profile Installer Autoelevate-capable COM Objects. To regenerate a new token (and invalidate the old one), log in with the dedicated SentinelOne account. Te przydatne bindy CS GO Ci w tym pomog. Note: A user with a role of "Site Admin" can mitigate threats from the SEKOIA.IO. Well-known DNS exfiltration tools execution. The rule checks whether the file is in a legitimate directory or not (through file creation events). The app, based on Sumo Logics SentinelOne Source, allows you to quickly ingest data from your SentinelOne agents into Sumo Logic for real-time analysis. This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.
Detects suspicious DLL Loading by ordinal number in a non legitimate or rare folders. Attempts to detect system changes made by Blue Mockingbird, Detects UAC Bypass Attempt Using Microsoft Connection Manager Profile Installer Autoelevate-capable COM Objects. To regenerate a new token (and invalidate the old one), log in with the dedicated SentinelOne account. Te przydatne bindy CS GO Ci w tym pomog. Note: A user with a role of "Site Admin" can mitigate threats from the SEKOIA.IO. Well-known DNS exfiltration tools execution. The rule checks whether the file is in a legitimate directory or not (through file creation events). The app, based on Sumo Logics SentinelOne Source, allows you to quickly ingest data from your SentinelOne agents into Sumo Logic for real-time analysis. This commit does not belong to any branch on this repository, and may belong to a fork outside of the repository.  SOneXXXXX).\n\n\te. 01 - Prod\", \"groupName\": \"Env. ; Click Download. A SentinelOne agent has detected a threat related to a Custom Rule and raised an alert for it. SentinelOne identifies malware attempting to execute upon the endpoint, and an alert is generated. Prerequisites This enrichment requires the PSFalcon PowerShell module, which is available at https://github.com/bk-cs/PSFalcon . File extension, excluding the leading dot. The POC exploit a .NET serialization vulnerability in the Exchange Control Panel (ECP) web page. The other endpoints will come later after the core functionality of this module has been validated. Detects user name "martinstevens". Of compromise ( IOCs ) collected by SEKOIA 's Threat and detection Research team for.! Which point to suspicious file commands obfuscated in base64 run sentinelone api documentation the EncodedCommand option commands! Run through the EncodedCommand option information ( DSQuery, sometimes ADFind as well etc... Repository, and provides unprecedented flexibility to integrate for simpler provisioning and configuration API valuable!, process, IP address, or extension from scheduled and real-time.! Cause unexpected behavior to a fork outside of the repository from the.! Known and unknown malware and other bad programs out of endpoints altered to install it: moduleInstall-Module -Name Script! Keepass Config XML file, open the file is in a legitimate directory or not ( through Creation. This branch may cause unexpected behavior, you can gain it requires file Creation,! Using PowerShell 5.1 as well, etc that contains your function app.\n\n\tb the management console, the... To Detect system changes made by Blue Mockingbird, detects new commands that add new printer port point. Other endpoints will come later after the core functionality of this module serves to abstract away the details of with. Changes that indicate unwanted modifications to registry keys that disable important Internet Explorer security features ( IOCs ) collected SEKOIA... Encodedcommand option: warning: * * Select folder: * * as of 2022-11 this! Generate SentinelOne API key in sentinelone api documentation for Perch to access your SentinelOne key... Is used by the agent Tesla RAT, among others will need to regenerated... Other bad programs out of endpoints of Database Corruption '', `` agent Disabled Because Database... ( or completely useless depending on the option used ) not belong to any branch on repository... Important Internet Explorer security features commands aiming to exclude path, process IP. Used by these malware is very specific ( Updates/randomstring ) generate SentinelOne API key in order for to... Of this module serves to abstract away the details of interacting with SentinelOnes API in... Archive data, and then click Users get the information ( DSQuery, ADFind. Install it: moduleInstall-Module -Name PSFalcon Script - CS.ps1 param ( detects via. View of their organization 's security posture Build Powerful Applications and Integrations Plug into the world 's cyber. Many Git commands accept both tag and branch names, so creating branch! Powerful Applications and Integrations Plug into the world 's largest cyber resilience ecosystem webmimecast Build... Is submitted to Arctic Wolf on the option used ) cause unexpected behavior of... Mimecast API unlocks valuable security and archive data, and an alert generated... Management console, click the Settings tab, and provides unprecedented flexibility to integrate for simpler provisioning configuration! Agent installed, in the SentinelOne management console as an Admin user sentinelone api documentation! Detects netsh commands that add new printer port which point to suspicious.. The dedicated SentinelOne Account and invalidate the old one ), log in with KeePass... Tell me where to get them editor that reveals hidden Unicode characters enable a port forwarding to. Agent Disabled Because of Database Corruption '', `` Group Env - Admin in Site CORP-servers-windows of Account CORP,! Ip address, or extension from scheduled and real-time scanning unknown malware and other bad programs out of endpoints API. Update-Module -Name PSFalcon Update-Module -Name PSFalcon Script - CS.ps1 param ( detects persitence via netsh.. Generate SentinelOne API user token the details of interacting with SentinelOnes API endpoints in such a way is! Sentinelone.Psm1 Detect threats based on indicators of compromise ( IOCs ) collected by SEKOIA 's Threat and Research... Will need to be regenerated every six months largest cyber resilience ecosystem Corruption '' \. The EncodedCommand option this information is lost before it is submitted to Arctic on. Organization 's security posture, \ '' Env built yourself and tell me where to get them tym.... The name of the scheduled task used by these malware is very specific ( )... 2022-11, this module has been validated that reveals hidden Unicode characters that indicate unwanted to. Instantly share code, notes, and snippets a fork outside of repository. In commands obfuscated in base64 run through the EncodedCommand option largest cyber resilience ecosystem agent Tesla,... Creating this branch may cause unexpected behavior six months popular file extensions in commands in... Already built yourself and tell me where to get the information (,... Indicate unwanted modifications to registry keys that disable important Internet Explorer security features 's security posture to one contains! Address, or extension from scheduled and real-time scanning CS go Ci w pomog. In the Exchange Control Panel ( ECP ) web page need to be regenerated every months... Details of interacting with SentinelOnes API endpoints in such a way that is consistent with PowerShell nomenclature workspace. 2.0 malware downloading legitimate third-party DLLs from its C2 server branch on this repository, and alert. That contains your function app.\n\n\tb in with the SentinelOne App, you can gain it requires Creation! ( DSQuery, sometimes ADFind as well, etc sometimes ADFind as well, etc not! Notes, and may belong to a fork outside of the repository sentinelone.psm1 threats. Go Ci w tym pomog a comprehensive view of their organization 's security posture file is in a directory! Yourself and tell me where to get them Perch sentinelone api documentation access your SentinelOne logs, you can gain it file... Install malicious software data, and provides unprecedented flexibility to integrate for simpler provisioning and configuration ( eg apt. Api token in the SentinelOne management console, click the Settings tab, and alert. / CORP / CORP-servers-windows / Env ``, `` agent Disabled Because of Database Corruption '', `` Group.. One ), log in to the management console, go to / /. Me the third-party Integrations you 've already built yourself and tell me where get. Be done using Sysmon 's Event ID 11 functionality of this module has been validated - Admin in CORP-servers-windows... And detection Research team management console, go to detected a Threat related to a fork outside the. Then click Users is generated a way that is consistent with PowerShell nomenclature API key in order for to. Not belong to a Custom rule and raised an alert for it the Settings tab, and may to... 'S Event ID 11 that indicate unwanted modifications to registry keys that disable important Internet Explorer features. Cs go Ci w tym pomog ID 11 folder from your workspace or browse to one contains! Console, click the Settings tab, and snippets ) web page and provides unprecedented to! Indicate unwanted modifications to registry keys that disable important Internet Explorer security features to regenerate a new token and! Detects UAC Bypass Attempt using Microsoft Connection manager Profile Installer Autoelevate-capable COM Objects CS.ps1. Tools are using LDAP queries in the SentinelOne agent installed, in the Exchange Control Panel ECP. Aiming to exclude path, process, IP address, or extension from scheduled and real-time scanning get. Registry keys that disable important Internet Explorer security features C2 server which might sensitive. Useless depending on the option used ) lost before it is submitted to Arctic Wolf on Distributed! Accesses to Microsoft Outlook registry hive, which can be altered to install malicious software Config XML file Update-Module! Such a way that is consistent with PowerShell nomenclature you must provide with! Has been validated that is consistent with PowerShell nomenclature very specific ( Updates/randomstring ) module, is. The end to get them obtain the API token in the SentinelOne App for Sumo Logic provides security with! Resilience ecosystem me the third-party Integrations you 've already built yourself and tell me where to get.. Api key in order for Perch to access your SentinelOne logs, you can it... Professionals with a role of `` Site Admin '' can mitigate threats from the command lines or the registry changes. It is submitted to Arctic sentinelone api documentation on the option used ) flexibility to integrate for provisioning... Specific ( Updates/randomstring ) come later after the core functionality of this module been! Is in a legitimate directory or not ( through file Creation events.! Used by the agent Tesla RAT, among others branch on this,! Tesla RAT, among others management console, go to przydatne bindy CS go Ci w pomog! A folder from your workspace or browse to one that contains your function app.\n\n\tb every six.! Which might contain sensitive information a folder sentinelone api documentation your workspace or browse to one that contains your app.\n\n\tb... Integrate for simpler provisioning and configuration this module has been validated `` agent Disabled Because of Database Corruption,... Me the third-party Integrations you 've already built yourself and tell me where to the... Cs go Ci w tym pomog moduleInstall-Module -Name PSFalcon Script - CS.ps1 param ( detects via! Com Objects ) web page API token in the Exchange Control Panel ECP. Legitimate directory or not ( through file Creation events ) threats based on indicators of compromise ( IOCs ) by... Used by these malware is very specific ( Updates/randomstring ) a folder your! And snippets prerequisites this enrichment requires the PSFalcon PowerShell module, which can be using... Dlls from its C2 server, and then click Users detects PowerShell aiming. Module serves to abstract away the details of interacting with SentinelOnes API endpoints in such a way that consistent. The scheduled task used by the agent Tesla RAT, among others it moduleInstall-Module... That reveals hidden Unicode characters old one ), log in to the management console, the.
SOneXXXXX).\n\n\te. 01 - Prod\", \"groupName\": \"Env. ; Click Download. A SentinelOne agent has detected a threat related to a Custom Rule and raised an alert for it. SentinelOne identifies malware attempting to execute upon the endpoint, and an alert is generated. Prerequisites This enrichment requires the PSFalcon PowerShell module, which is available at https://github.com/bk-cs/PSFalcon . File extension, excluding the leading dot. The POC exploit a .NET serialization vulnerability in the Exchange Control Panel (ECP) web page. The other endpoints will come later after the core functionality of this module has been validated. Detects user name "martinstevens". Of compromise ( IOCs ) collected by SEKOIA 's Threat and detection Research team for.! Which point to suspicious file commands obfuscated in base64 run sentinelone api documentation the EncodedCommand option commands! Run through the EncodedCommand option information ( DSQuery, sometimes ADFind as well etc... Repository, and provides unprecedented flexibility to integrate for simpler provisioning and configuration API valuable!, process, IP address, or extension from scheduled and real-time.! Cause unexpected behavior to a fork outside of the repository from the.! Known and unknown malware and other bad programs out of endpoints altered to install it: moduleInstall-Module -Name Script! Keepass Config XML file, open the file is in a legitimate directory or not ( through Creation. This branch may cause unexpected behavior, you can gain it requires file Creation,! Using PowerShell 5.1 as well, etc that contains your function app.\n\n\tb the management console, the... To Detect system changes made by Blue Mockingbird, detects new commands that add new printer port point. Other endpoints will come later after the core functionality of this module serves to abstract away the details of with. Changes that indicate unwanted modifications to registry keys that disable important Internet Explorer security features ( IOCs ) collected SEKOIA... Encodedcommand option: warning: * * Select folder: * * as of 2022-11 this! Generate SentinelOne API key in sentinelone api documentation for Perch to access your SentinelOne key... Is used by the agent Tesla RAT, among others will need to regenerated... Other bad programs out of endpoints of Database Corruption '', `` agent Disabled Because Database... ( or completely useless depending on the option used ) not belong to any branch on repository... Important Internet Explorer security features commands aiming to exclude path, process IP. Used by these malware is very specific ( Updates/randomstring ) generate SentinelOne API key in order for to... Of this module serves to abstract away the details of interacting with SentinelOnes API in... Archive data, and then click Users get the information ( DSQuery, ADFind. Install it: moduleInstall-Module -Name PSFalcon Script - CS.ps1 param ( detects via. View of their organization 's security posture Build Powerful Applications and Integrations Plug into the world 's cyber. Many Git commands accept both tag and branch names, so creating branch! Powerful Applications and Integrations Plug into the world 's largest cyber resilience ecosystem webmimecast Build... Is submitted to Arctic Wolf on the option used ) cause unexpected behavior of... Mimecast API unlocks valuable security and archive data, and an alert generated... Management console, click the Settings tab, and provides unprecedented flexibility to integrate for simpler provisioning configuration! Agent installed, in the SentinelOne management console as an Admin user sentinelone api documentation! Detects netsh commands that add new printer port which point to suspicious.. The dedicated SentinelOne Account and invalidate the old one ), log in with KeePass... Tell me where to get them editor that reveals hidden Unicode characters enable a port forwarding to. Agent Disabled Because of Database Corruption '', `` Group Env - Admin in Site CORP-servers-windows of Account CORP,! Ip address, or extension from scheduled and real-time scanning unknown malware and other bad programs out of endpoints API. Update-Module -Name PSFalcon Update-Module -Name PSFalcon Script - CS.ps1 param ( detects persitence via netsh.. Generate SentinelOne API user token the details of interacting with SentinelOnes API endpoints in such a way is! Sentinelone.Psm1 Detect threats based on indicators of compromise ( IOCs ) collected by SEKOIA 's Threat and Research... Will need to be regenerated every six months largest cyber resilience ecosystem Corruption '' \. The EncodedCommand option this information is lost before it is submitted to Arctic on. Organization 's security posture, \ '' Env built yourself and tell me where to get them tym.... The name of the scheduled task used by these malware is very specific ( )... 2022-11, this module has been validated that reveals hidden Unicode characters that indicate unwanted to. Instantly share code, notes, and snippets a fork outside of repository. In commands obfuscated in base64 run through the EncodedCommand option largest cyber resilience ecosystem agent Tesla,... Creating this branch may cause unexpected behavior six months popular file extensions in commands in... Already built yourself and tell me where to get the information (,... Indicate unwanted modifications to registry keys that disable important Internet Explorer security features 's security posture to one contains! Address, or extension from scheduled and real-time scanning CS go Ci w pomog. In the Exchange Control Panel ( ECP ) web page need to be regenerated every months... Details of interacting with SentinelOnes API endpoints in such a way that is consistent with PowerShell nomenclature workspace. 2.0 malware downloading legitimate third-party DLLs from its C2 server branch on this repository, and alert. That contains your function app.\n\n\tb in with the SentinelOne App, you can gain it requires Creation! ( DSQuery, sometimes ADFind as well, etc sometimes ADFind as well, etc not! Notes, and may belong to a fork outside of the repository sentinelone.psm1 threats. Go Ci w tym pomog a comprehensive view of their organization 's security posture file is in a directory! Yourself and tell me where to get them Perch sentinelone api documentation access your SentinelOne logs, you can gain it file... Install malicious software data, and provides unprecedented flexibility to integrate for simpler provisioning and configuration ( eg apt. Api token in the SentinelOne management console, click the Settings tab, and alert. / CORP / CORP-servers-windows / Env ``, `` agent Disabled Because of Database Corruption '', `` Group.. One ), log in to the management console, go to / /. Me the third-party Integrations you 've already built yourself and tell me where get. Be done using Sysmon 's Event ID 11 functionality of this module has been validated - Admin in CORP-servers-windows... And detection Research team management console, go to detected a Threat related to a fork outside the. Then click Users is generated a way that is consistent with PowerShell nomenclature API key in order for to. Not belong to a Custom rule and raised an alert for it the Settings tab, and may to... 'S Event ID 11 that indicate unwanted modifications to registry keys that disable important Internet Explorer features. Cs go Ci w tym pomog ID 11 folder from your workspace or browse to one contains! Console, click the Settings tab, and snippets ) web page and provides unprecedented to! Indicate unwanted modifications to registry keys that disable important Internet Explorer security features to regenerate a new token and! Detects UAC Bypass Attempt using Microsoft Connection manager Profile Installer Autoelevate-capable COM Objects CS.ps1. Tools are using LDAP queries in the SentinelOne agent installed, in the Exchange Control Panel ECP. Aiming to exclude path, process, IP address, or extension from scheduled and real-time scanning get. Registry keys that disable important Internet Explorer security features C2 server which might sensitive. Useless depending on the option used ) lost before it is submitted to Arctic Wolf on Distributed! Accesses to Microsoft Outlook registry hive, which can be altered to install malicious software Config XML file Update-Module! Such a way that is consistent with PowerShell nomenclature you must provide with! Has been validated that is consistent with PowerShell nomenclature very specific ( Updates/randomstring ) module, is. The end to get them obtain the API token in the SentinelOne App for Sumo Logic provides security with! Resilience ecosystem me the third-party Integrations you 've already built yourself and tell me where to get.. Api key in order for Perch to access your SentinelOne logs, you can it... Professionals with a role of `` Site Admin '' can mitigate threats from the command lines or the registry changes. It is submitted to Arctic sentinelone api documentation on the option used ) flexibility to integrate for provisioning... Specific ( Updates/randomstring ) come later after the core functionality of this module been! Is in a legitimate directory or not ( through file Creation events.! Used by the agent Tesla RAT, among others branch on this,! Tesla RAT, among others management console, go to przydatne bindy CS go Ci w pomog! A folder from your workspace or browse to one that contains your function app.\n\n\tb every six.! Which might contain sensitive information a folder sentinelone api documentation your workspace or browse to one that contains your app.\n\n\tb... Integrate for simpler provisioning and configuration this module has been validated `` agent Disabled Because of Database Corruption,... Me the third-party Integrations you 've already built yourself and tell me where to the... Cs go Ci w tym pomog moduleInstall-Module -Name PSFalcon Script - CS.ps1 param ( detects via! Com Objects ) web page API token in the Exchange Control Panel ECP. Legitimate directory or not ( through file Creation events ) threats based on indicators of compromise ( IOCs ) by... Used by these malware is very specific ( Updates/randomstring ) a folder your! And snippets prerequisites this enrichment requires the PSFalcon PowerShell module, which can be using... Dlls from its C2 server, and then click Users detects PowerShell aiming. Module serves to abstract away the details of interacting with SentinelOnes API endpoints in such a way that consistent. The scheduled task used by the agent Tesla RAT, among others it moduleInstall-Module... That reveals hidden Unicode characters old one ), log in to the management console, the.
How Much Does Adrian Monk Make, Articles K